Wireless Ad Hoc Network Security
I would like to discuss about prevailing security issues in wireless adhoc network through this post.
In modern world, the applications of ad hoc network are emerging rapidly
as its feasibility of usage is higher when comparing with other existing wireless
solutions and it’s relatively low cost. It has no any infrastructure and it is a peer
to peer (host to host) self organizing network. Though ad hoc network is very
popular and enlarging network, there are some security issues which are being
gone to discuss in this survey report. According to the applications, wireless ad
hoc networks can be clarified as following
- Mobile Ad hoc networks(MANETs)
- Wireless mesh networks
- Wireless sensor networks
In real scenario, ad hoc network is used widely in military operations and
other security related tasks. Securing ad hoc network implies, identifying currently
existing issues and presenting assumptions to solve those issues such as
secure routing protocols, intruder detection and response and etc. Identifying
such vulnerabilities of security attacks might help to improve better wireless ad
hoc network with higher security.
Basically there are number of security holes in ad hoc networks. Some major
issues have been illustrated below.
- The main uncertainty of ad hoc network is its susceptibility to attacks which can be categorized as passive attacks and active attacks.
- Inability of keeping trust due to a difficulty of deploying trusted third party such as Certificate Authority (CA).
- Routing Protocol problems.
Passive attack subverts the parties those who want to communicate in confident
manner. It violates confidentiality by giving an adversary to access secret
information but does not do any tangible damage to message such as deleting
or inserting unlike active attack does.
The main goal of routing protocols in ad hoc network is that it should be
capable of cope with changing topologies. Though such protocols exist today,
it cannot provide considerable security against malicious attacks from external
and internal dissentienters. As this routing protocol for ad hoc networks are
still in research category, identifying and capturing such routing security issues
lead a path for implementing better routing protocol.
Due to dynamic behavior of changing topology of ad hoc network, it is hard
to consider of trusted third party and any single node cannot trust either. So
without depending on one entity, it is better to have distributed architecture
instead of centralized architecture for ad hoc network.
Unlike wired networks, wireless network carries on its task in a hostile environment with lack of physical protections. This is also a case to arise security issues as a result of compromisation. So it is another challenge to pay attention in aspect of both internally and externally. So attacks could possibly enter not only from outside the network but also from inside the network. As mentioned earlier in addition to major security concerns, here survivability comes into play. So one of the major challenge among other is that ad hoc network should have distributed structure instead of centralized structure. So unlike in centralized concept, though one node is compromised, others can still survive within the network as its distributed structure.
Another challenge is its scope of nodes. As ad hoc networks are growing rapidly by connecting nodes, its scope gets larger gradually. In order to protect each nodes attach to network there should be a strong security mechanism. Above mentioned challenges can be clari ed into three major ways
Another challenge is its scope of nodes. As ad hoc networks are growing rapidly by connecting nodes, its scope gets larger gradually. In order to protect each nodes attach to network there should be a strong security mechanism. Above mentioned challenges can be clari ed into three major ways
- Secure Routing problems in prevailing ad hoc protocols
- Key Distribution
- Link Level Security
Key Distribution in Wireless Adhoc Networks
Using a shared key distribution policy, wireless ad hoc networks enable each party to trust each
other those who are communicating with other in same group. Basic idea behind key distribution is
something like common session key sharing with all parties in order to communicate in a secure way.
This scenario highly guarantees authenticity of individuals in conference. Problem comes into stage
when thinking who is going to distribute key among others who are active node in ad hoc environment.
To achieve this, there should be a centralized key distribution mechanism such as Certi cate Authority.
Within a Public Key Infrastructure (PKI) CA issues public keys to each and every node in order to
maintain mutual trust between nodes in ad hoc network. Depending on one centralized entity may
cause severe damage to entire system if it is compromised. Not only is that, to implement such a
protocol also a complex task due to non continuous connectivity between nodes.
Such protocol has to cope with major security concerns and should have a resistance against above
mentioned basic two problems.
Expecting properties for such a protocol
- Secrecy : Attending members should only know the secret key, eg: session key
- Perfect Forward Secrecy : Dynamically changing session key causes intruder to unpredicted the nest session key when group of users get together in next time.
- Contributory key agreement : If each and every player participates in the creation of the final session key, by making a contribution, then it is called contributory key agreement.
- Tolerance to disruption attempts : Content of the message cannot be modi ed or deleted.
Secure Routing
Existing routing protocols work ne with changing topology. But it is not that much of considered
about their security aspect since the probability for susceptible to attack is greater. As there are
no any prede ned standard protocol exist for ad hoc routing, attackers can gain advantage of it.
In ad hoc environment routers communicate with each other informally in order to establish routes
between nodes. This enables wireless link attack such as eavesdropping, spoo ng, denial of service,
masquerading and impersonation which will be further explained under secure routing methodologies.
Though one intends secure routing protocol that provides higher security goals to the system, that
system should be able to perform its task such as routing and forwarding in an e cient and corrective
way.
As security has become an essential concept in ad hoc networks, above mentioned points are expected
to cover. In this article I focus on the fundamental security issues of protecting ad hoc network
connectivity between nodes.
Routing Paradigm
The main goal of routing protocols in ad hoc network is that it should be capable of cope with changing
topologies. Though such protocols exist today, it cannot provide considerable security against mali-
cious attacks from external and internal dissentienters. Injecting erroneous routing info, pretending
by extracting past routing info and distorting routing info can be pointed out as external attacks from
which entire network can bring down by reducing its performance. Internal attackers imply internally
veri cation of each node that is participated to route routing info. Validity of each node signature is
considered by signing each node when carries info, so hard to detect and correct due to compromised
nodes also can generate valid signatures using their private keys and so this is complex task to capture
since ad-hoc network comes into play in changing topology.
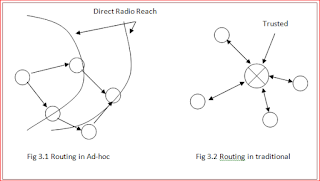
Infrastructure
Routing in ad hoc Vs Routing in traditiional
- No any centralized entity
- Individual node carries routing info
- When Communicating with far apart nodes, routing depends on intermediate nodes to routemessage to them
Problems - Routing in Ad-hoc
Assumptions-
These assumptions are made by considering existing routing protocols (not all, some routing protocols
which only cope with dynamically changing topology). But if they are violated, entire network is in
risk.
- All nodes in ad hoc environment are cooperative with each other
- All nodes are trustworthy
- If key is shared among entities, it is generated by single entity
Implicit Trust relationship between neighbors
Each node implicitly keeps trust on their neighbor and route packets depending on nodes in precinct.
Intruder can inject malicious routing info in order to bring down the network.
Throughput
Main two tasks are carried out by ad hoc network which can be clari ed as routing and forwarding.
Increasing number of time this takes place can be considered as increasing network throughput. But
what if a single node begins to drop packets or present signs of overloading or brake because of intruder
attack. As entire network depend on each others, misbehaving even one node can be a significant
problem, so in the worst case it will be very critical point to pay attention.
Attacks using modi cation of protocol elds of messages
Routing protocols packets have a eld which contains important control information. This eld is not
altered by any nodes when packet transmission is taken place among nodes. But malicious nodes can
alter this eld and so it will eventually cause redirection of network tra c and DoS attacks by altering
this field.
1. Remote redirection of modified route sequence number (AODV)
Remote redirection attacks are also called black hole attacks. In the attacks, a malicious node
uses routing protocol to advertise itself as the shortest path to nodes whose packets it wants to
intercept. Protocols such as AODV instantiate and maintain routes by assigning monotonically
increasing sequence numbers to routes towards a speci c destination. In AODV, any node may
divert traffic through itself by advertising a route to a node with a destination sequence number
greater than the authentic value.
2. Redirection with modi ed hop count (AODV)
A redirection attack is also possible in certain protocols, such as AODV, by modi cation of the
hop count eld in route discovery messages. When routing decisions cannot be made by other
metrics, AODV uses the hop count eld to determine a shortest path. In AODV, malicious
nodes can attract route towards themselves by resetting the hop count eld of the RREP to
zero. Similarly, by setting the hop count eld of the RREP to in nity, routes will tend to be
created that do not include the malicious node.
Attacks using impersonation
Existing ad hoc routing protocols do not authenticate source node IP address. Intruder can make use
of this security hole to preclude to the ad hoc environment.
Lack of self-stabilization property
Availability is a major security concern. After intruder attack happened, there should be a recovery
process in order to survive, make ad hoc network stabilize and visible to users without spoo ng data.
An intruder should not be able to permanently disable a network by injecting a smaller number of
mal-informed routing packets. E.g. AODV, however is prone to self-stabilization problems as sequence
numbers are used to verify route validity times, and incorrect state may remain stored in the routing
tables for a long time.
Easily leak information about network topology
Con dentiality is another major security concern. But ad-hoc routing protocols like AODV and DSR